Microsoft has released security updates for 84 vulnerabilities in its October 2022 Patch Tuesday Edition. The security updates addressed two zero-days with one actively exploited in attacks (CVE-2022-41033) and one publicly disclosed (CVE-2022-41043). Out of the 84 vulnerabilities, 13 are rated critical (privilege elevation, spoofing, remote code execution, and other severe types of vulnerabilities).
It is important to note that Microsoft didn’t release fixes for the two Exchange Server zero-days (CVE-2022-41040 and CVE-2022-41082) (ProxyNotShell). These vulnerabilities were exploited in late September. Microsoft has released mitigations and workarounds for these vulnerabilities.
Microsoft also included 12 updates for Microsoft Edge (Chromium-based) vulnerabilities in this Patch Tuesday edition. One of them was a spoofing vulnerability that had been patched earlier this month.
The advisory covers a total of 52 products, features, and roles, including Windows TCP/IP, Windows Point-to-Point Tunneling Protocol, Windows Group Policy Preference Client, Windows Internet Key Exchange (IKE) Protocol, Azure Arc, Active Directory Domain Services, Windows Hyper-V, Visual Studio Code, and many more.
The vulnerabilities are classified as follows:
- Spoofing Vulnerability: 4
- Denial of Service Vulnerability: 8
- Elevation of Privilege Vulnerability: 39
- Security Feature Bypass Vulnerability: 2
- Information Disclosure Vulnerability: 11
- Remote Code Execution Vulnerability: 20
Zero-day vulnerabilities addressed in Patch Tuesday, October 2022 Edition
Windows COM+ Event System Service Elevation of Privilege Vulnerability (CVE-2022-41033)
This elevation of privilege vulnerability was caused by a flaw in the COM+ Event System Service. This flaw can automatically distribute events to Component Object Model (COM) components. An attacker could exploit this vulnerability by executing specially crafted code. On successful exploitation, an attacker could gain SYSTEM privileges and will be able to execute arbitrary code. This vulnerability is said to be exploited in the wild.
Microsoft Office Information Disclosure Vulnerability (CVE-2022-41043)
This vulnerability was discovered by Cody Thomas with SpecterOps. This Information Disclosure vulnerability affects Office for Mac. The flaw is publicly disclosed but not yet seen exploited in the wild. On successful exploitation of this flaw, an attacker could expose user tokens and other potentially sensitive information.
Some of the critical vulnerabilities addressed in Patch Tuesday, October 2022 Edition
CVE-2022-37968: Azure Arc-enabled Kubernetes cluster Connect Elevation of Privilege Vulnerability
This vulnerability exists in Azure Arc but could also impact the Kubernetes cluster and Azure Stack Edge that is connected to the vulnerable Azure Arc.
An attacker with the knowledge of randomly generated external DNS endpoint for a Kubernetes cluster running on Azure Arc can exploit this vulnerability online. An unauthenticated user can elevate their privileges to that of a cluster admin and potentially take over the Kubernetes cluster by successfully exploiting this vulnerability, which affects the cluster connect capability of Azure Arc-enabled Kubernetes clusters.
CVE-2022-38048: Microsoft Office Remote Code Execution Vulnerability
Microsoft has credited Jarvis_1oop, Yuki Chen with Cyber KunLun, and hades_kito for working with Trend Micro Zero Day Initiative for discovering the vulnerability. The attack is carried out locally by a remote attacker. An attacker would have to create a file intended to take advantage of this flaw and send it to a victim.
CVE-2022-41038: Microsoft SharePoint Server Remote Code Execution Vulnerability
An attacker needs to have permission to use Manage Lists within SharePoint along with the authentication to the target site to exploit this vulnerability. An authenticated attacker could remotely run a malicious code on the SharePoint Server in a network-based attack environment on successful exploitation of this vulnerability.
CVE-2022-37976: Active Directory Certificate Services Elevation of Privilege Vulnerability
In order to execute a cross-protocol attack, a malicious DCOM client could force a DCOM server to authenticate to it via the Active Directory Certificate Service (ADCS). On successful exploitation, an attacker could gain domain administrator privileges.
CVE-2022-34689: Windows CryptoAPI Spoofing Vulnerability
This vulnerability was discovered by the UK National Cyber Security Centre (NCSC) and the National Security Agency (NSA). An attacker might use an active public x.509 certificate to spoof the targeted certificate and carry out actions like authentication or code signing.
CVE-2022-37979: Windows Hyper-V Elevation of Privilege Vulnerability
An attacker will be required to win a race condition to exploit this vulnerability. On Successful exploitation, this vulnerability could allow a Hyper-V guest to affect the functionality of the Hyper-V host. An attacker on a Nested Hyper-V environment would gain Level 1 Hyper-V Windows Root OS privileges.
CVE-2022-22035, CVE-2022-24504, CVE-2022-30198, CVE-2022-33634, CVE-2022-38000, CVE-2022-38047, CVE-2022-41081: Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerabilities
These vulnerabilities were discovered by Yuki Chen with Cyber KunLun. An attacker would need to send a specially crafted malicious PPTP packet to a PPTP server to exploit these vulnerabilities. For successful exploitation, an attacker would need to win a race condition. Successful exploitation of these flaws could result in remote code execution on the server side.
Evaluating workaround using Qualys Policy Compliance (PC)
Qualys Policy Compliance customers can evaluate workarounds based on the following controls:
CVE-2022-37976: Active Directory Certificate Services Elevation of Privilege Vulnerability
4079 Status of the ‘Active Directory Certificate Service’
14916 Status of Windows Services
24842 Status of the ‘LegacyAuthenticationLevel’ setting
CVE-2022-33645: Windows TCP/IP Driver Denial of Service Vulnerability
4842 Status of the ‘Internet Protocol version 6 (IPv6) components’ setting
Executing workaround using Qualys Custom Assessment and Remediation (CAR)
Customers can perform the provided mitigation steps by creating a PowerShell script and executing it on vulnerable assets.
Try It for Free
Sign up for a no-cost trial of Qualys Custom Assessment and Remediation.
CVE-2022-37976: Active Directory Certificate Services Elevation of Privilege Vulnerability
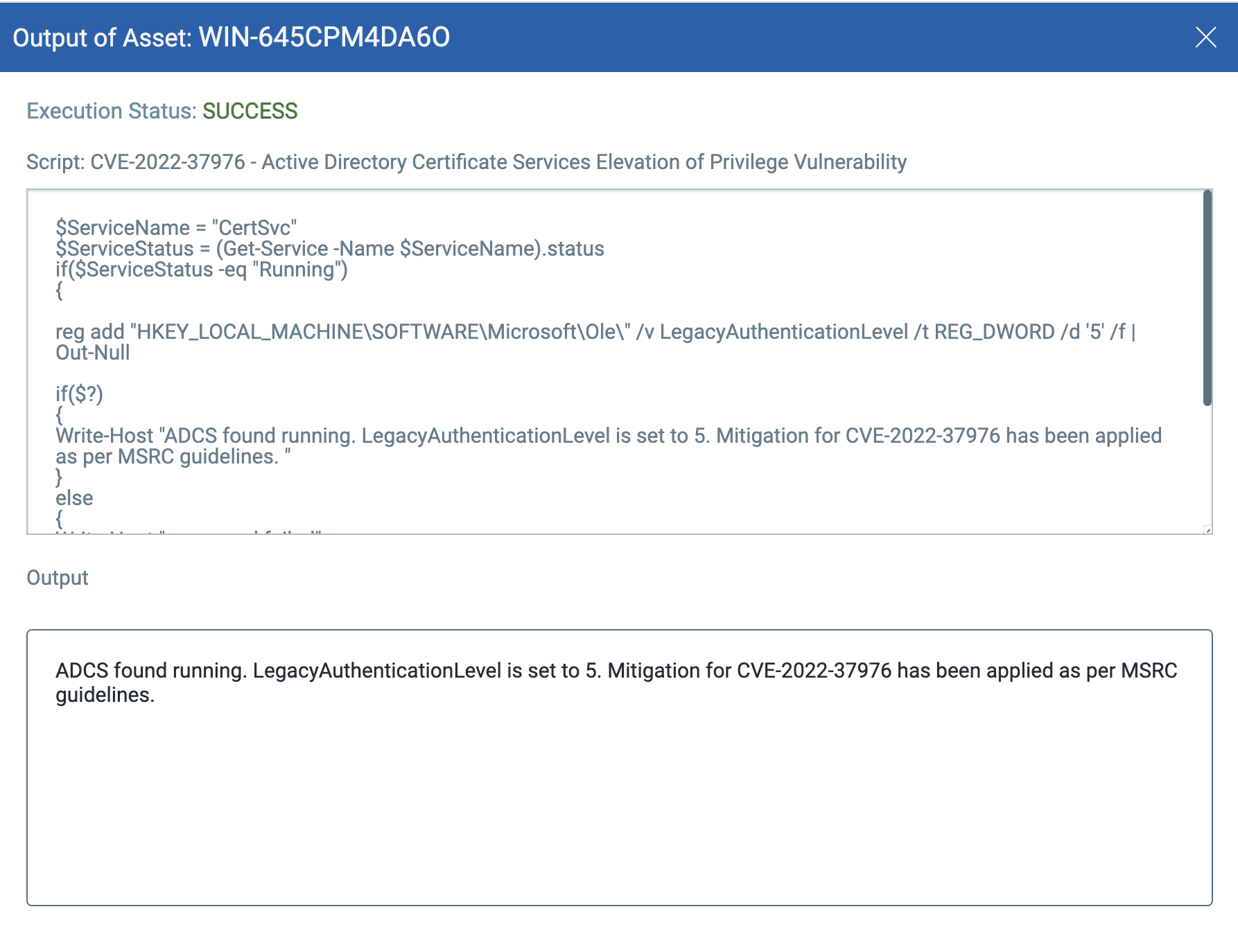 Script is available in Qualys library
Script is available in Qualys library
CVE-2022-33645: Windows TCP/IP Driver Denial of Service Vulnerability
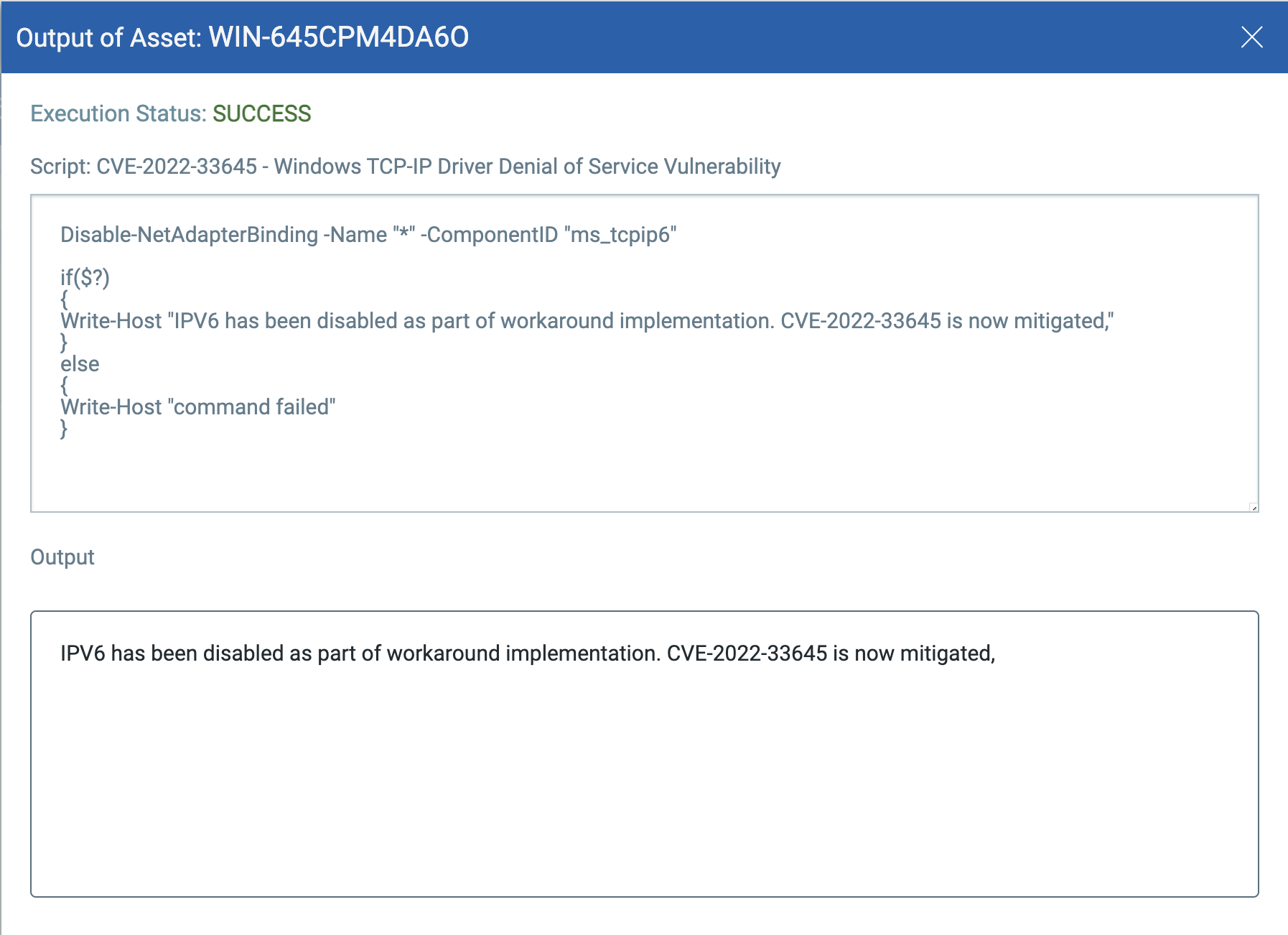
Script is available in Qualys library
Visit the October 2022 Security Updates page to access the full description of each vulnerability and the systems it affects.
Qualys customers can scan their network with QIDs 91953, 377628, 110418, 110417, 91951, 91950, 91949, and 377627 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References:
https://msrc.microsoft.com/update-guide/
https://msrc.microsoft.com/update-guide/releaseNote/2022-Oct
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41033
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41043
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-37968
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-38048
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-37976
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-34689
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-37979
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-22035
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-24504
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-30198
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-33634
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-38000
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-38047
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41081